As ransomware attacks continue to dominate headlines, organizations everywhere are rethinking their cybersecurity postures. Criminals target not just primary systems but also backup repositories, encrypting or destroying them in order to demand a large ransom. According to recent industry reports, ransomware attacks grew by over 130% between 2020 and 2022, costing billions in damages worldwide.
The problem is that traditional backups often rely on copies that can be edited or wiped. Attackers know this. They try to compromise backups before you can restore data. If that happens, you might have no choice but to pay or face major outages.
This is where backups that cannot be changed within a set time—immutable backups—come in. These backups stay untouchable no matter who tries to access them. Many regulations now expect or demand this approach to protect privacy and reduce risk.
Read on to learn how immutability works, why it matters, and how you can use it. You will also learn how one client dodged a ransom payment when attackers wiped out their usual backups.
What Are Immutable Backups?
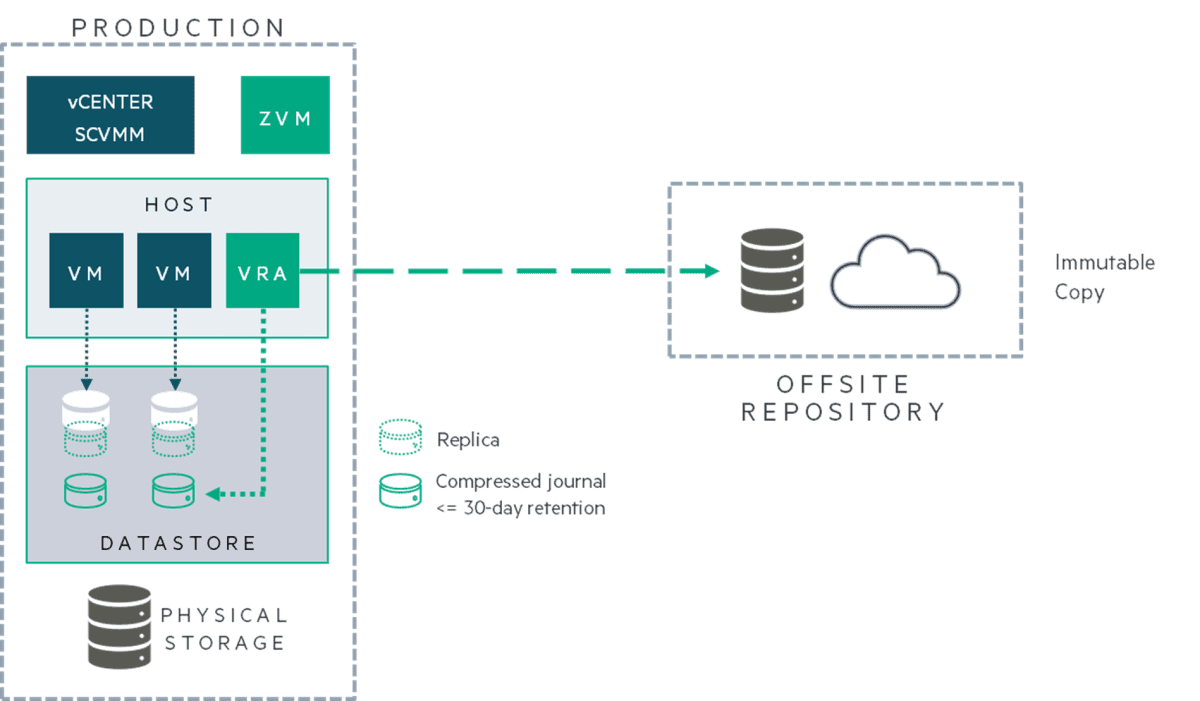
An immutable backup is a copy of your data that no one can change or remove until a set time expires. You store it once and read it whenever you want, but you cannot edit it. Even if someone has administrator rights, they cannot remove or modify it until that retention clock runs out.
Think of it as a sealed container. You lock it and only open it again at the chosen date. That blocks ransomware from encrypting or deleting data. It also prevents anyone inside your organization from removing important records by mistake.
Why you need this:
- You stop attackers from taking away your best path to recovery.
- You protect yourself from insider mistakes or sabotage.
- You match rules that require data integrity.
- You keep a read-only version of your data with fewer ways for threats to break in.
In a time when criminals look for backup repositories, immutability is a direct answer. It is a plain way to store data and then keep it locked. That tactic can spare you from paying large ransoms and losing trust. It sets you up to bounce back from an attack.
The Growing Need for Immutability in Data Protection
Attackers are eager to earn money by seizing your information. They may spend days or weeks inside your network to learn your backup strategy. Then they strike backups first, blocking your ability to restore.
Sometimes, employees or simple errors remove or change files, which creates a different type of crisis. Government and industry rules make these threats harder to ignore. You may have to keep certain data sets unchanged for legal or privacy mandates.
You might see these trends in day-to-day operations:
- Ransomware groups are more aggressive than ever. They encrypt systems and backups simultaneously and demand payment.
- Threats come from inside your business. An upset employee or an administrator who picks the wrong option can erase important data.
- Government rules, such as HIPAA or GDPR, set penalties if you cannot prove your data is intact.
- You might keep data in many places, including on-premises servers and cloud platforms. That spread can create confusion about how to store and protect each copy.
Immutable backups can remove many headaches. If someone tries to wipe or encrypt your data, they hit a locked copy that sits safely in a separate location. That means you have a genuine fallback if your main environment or standard backups are locked or removed.
Object Locking Explained
Object locking is a storage feature that stops anyone from removing or changing data for a chosen stretch of time. It follows the principle of “write once, read many times.” Once the object is stored, it remains in place. Even administrators cannot erase it until the retention date arrives.
Many S3-compatible platforms include this feature. You set a mode, such as compliance or governance, then pick how long to hold the data. You might add a legal hold if you need to keep data for an investigation. In compliance mode, nobody can shorten or skip the retention schedule. It is a direct way to keep your backups safe from intruders who grab credentials or from errors by your own team.
This approach prevents the nightmare where someone logs in with high-level rights and tries to remove your entire backup set. The locked data is still there once you detect the attack and kick the intruder out.
How Stage2Data Uses Object Locking to Safeguard Data
Stage2Data focuses on data backups, recovery, and hosting. Object locking is a key part of our storage platform. You store backups in an S3-based system that follows a strict write-once method. Then, a timer blocks changes until the clock runs out.
Here are the main pieces of our setup:
- Immutable Storage: We work with secure object storage where you pick a retention period that fits your needs. Nobody can remove or alter backups during that time.
- Multiple Layers: We connect object locking with replication tools like Zerto or Veeam. This allows immediate failover in many situations. You also have the locked copy if attackers break through the main environment.
- Hybrid Support: We can protect data on-premises or in the cloud. We keep the locking process consistent across your entire setup.
- Monitoring and Alerts: You receive notices if new data sets appear or if retention settings change. This transparency helps you confirm that your backups remain safe.
- Security Mindset: We assume attackers might get inside your main network. Locked backups sit beyond their reach. Even if they grab admin credentials, the backups still cannot be removed.
This adds up to a steady fallback. You can trust that a read-only copy of your data sits in a secure place, waiting if everything else fails. That copy is especially helpful if your primary site or standard replicas are erased or encrypted.
Case Example: An Intruder Hijacked a Backup Console, Yet the Client Paid No Ransom
A Stage2Data client lost every local server and off-site replication in a late-night attack. An intruder with high-level access hijacked the Zerto console, deleted the local Zerto setup, and removed the VPGs in the cloud. The attacker planned to force a ransom payment by destroying direct recovery paths.
Stage2Data had set up locked S3 backups that used object locking to block changes until the retention period ended. The attacker missed these backups, which stayed safe in a separate location. The Stage2Data team restored critical servers in about an hour by testing the data for malware and spinning up new environments on Stage2Data’s infrastructure.
We used Network Recovery-as-a-Service™ (NRaaS) to route the client’s internet-facing services. That freed them from the hacked site. After seeing how quickly the restore worked, the client moved their entire hosting to Stage2Data’s IaaS. By pairing Zerto’s long-term retention with locked backups, they skipped ransom demands and saved valuable time.
Stage2Data and Zerto’s immutable backups saves customer from severe ransomware breach
Immutable Backups vs. Other Backup Strategies
You might wonder how immutability compares to other methods. Here are some common options:
- Air-Gapped Backups: You store data on offline media, such as tape. It is hard for an intruder to access offline copies. But moving data on and off tape can slow you down, and you might not test those backups as often as you want.
- Snapshots: These point-in-time copies are quick to make and quick to restore. But if someone with administrator rights removes them, you lose that layer.
- Replication: This creates a near-identical copy of your environment in another location. It helps if you have hardware failures or a local incident. But if malware spreads or if someone wipes the primary copy, that damage may carry over to the target as well.
Immutable backups fill that final gap by storing a read-only set of data. You might still rely on replication for fast failover, then turn to immutability if you need a protected version that no one has touched. By mixing these methods, you cover speed, reliability, and deep protection.
Final Thoughts: Make Immutability Non-Negotiable
If you lose your backups, your recovery plan may collapse. Attackers often remove or encrypt backup files before asking for money. Without a safe copy, you might face an unpleasant choice: pay a ransom or watch your data vanish. Locked backups with object storage avoid that scenario. They stay read-only until a set date, no matter who tries to tamper with them.
You might keep these points in mind:
- Treat immutability as a key part of your backup plan.
- Lock backups in a place that intruders cannot modify, even if they have administrator rights.
- Use layered protection. Combine immutability with replication or snapshots for fast recovery in simpler failures, and rely on the locked copy if an intruder wipes out the usual route.
- Keep your staff informed. Backups must be tested and monitored. You want to know if someone tries to remove or change data.
Many businesses find that locked backups give them the confidence to meet threats. You do not need to pay ransom or wonder if your data is gone for good. The plan is simple: you write the data once, then lock it until time is up. That keeps you in charge and thieves out.
Join the Stage2Data Partner Program
The DRaaS market is growing fast, and MSPs have an incredible opportunity to lead the way. Partnering with Stage2Data means offering your clients more than just disaster recovery. It means giving them better value, service, and peace of mind—all while growing your own business.
Getting started is easy. Our team will guide you through the process, from initial setup to training and beyond. You’ll have access to the tools and support you need to succeed, all without the red tape that comes with larger providers.






