Ransomware in 2025 didn’t “shift.” It kept doing what it has always done, just with sharper tradecraft and fewer wasted moves. Attackers still lock up systems, but they spend more effort getting reliable entry, stealing data, and breaking recovery plans in ways that don’t show up in a backup dashboard.
This puts more pressure on your recovery plans to answer two basic questions fast: can you restore clean systems, and can people reach them when the primary network is unsafe. For those leading IT, security, or connectivity planning, 2025’s numbers point to three practical priorities:
- Clean recovery and the ability to restore without bringing the attacker back with you;
- Network reachability; and
- Cloud independence as a way out when your primary cloud or tenant becomes the problem.
This post breaks down what 2025 reporting means for disaster recovery planning and day-to-day ransomware recovery decisions.
What 2025 Reporting Says About Ransomware and Recovery
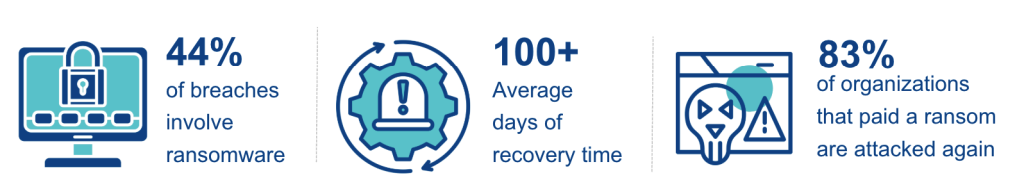
A few datapoints set the tone. Verizon’s 2025 DBIR Report found ransomware present in 44% of the breaches reviewed, up from 32% the prior year. The median ransom paid fell to $115,000, and 64% of victim organizations did not pay. At the same time, the exploitation of vulnerabilities as an initial access vector rose to 20%, with a significant increase in edge devices and VPN targets within that set. Third-party involvement in breaches doubled from 15% to 30%.
IBM’s 2025 Cost of a Data Breach highlights the metric that defined the year: recovery took more than 100 days on average. This delay often occurred because organizations lacked Locked Object Storage, allowing attackers to manipulate or delete backup metadata even if the data itself was immutable.
Additionally, Sophos’ State of Ransomware 2025 report notes that data encryption fell to 50% of attacks, down from 70% in 2024. Yet data theft still shows up, and backups did not carry the load every time: victims used backups to restore encrypted data in 54% of incidents, and 49% paid to get data back.
Another hard lesson from incident reporting is repeat risk. Research shows 83% of organizations that paid the ransom still faced follow-on attacks. This confirms that payment does not remove the underlying threat or the attacker’s access.
The lesson from 2025 is clear: Organizations that relied on basic, short-term snapshots failed. The victories belonged to those who implemented Long-Term Retention (LTR) to find clean recovery points from before the initial compromise.
The 2026 Technical Standard: LTR, EJC, and Locked Object Storage
To bridge the gap between “restored” and “operational,” 2026 strategies must incorporate three specific technical pillars:
- Locked Object Storage: Traditional backups are now primary targets. By using S3 Object Lock or similar “write once, read many” (WORM) protocols, you ensure that even a compromised administrator account cannot delete your recovery path.
- Long-Term Retention (LTR): With attacker dwell times still averaging weeks, a 14-day backup rotation is insufficient. LTR allows you to reach back to a state before the “silent” phase of an attack began.
- Enhanced Job Control (EJC): Recovery is not a bulk event. EJC allows for granular orchestration, ensuring identity services are restored and hardened before application data is ever touched.
Clean Recovery: “Restored” Isn’t the Same as “Back to Normal”
Many recovery plans still treat ransomware like a storage problem: recover snapshots, bring up systems, and move on. That plan fails in two common ways.
First, teams restore from immutable backups that look healthy but contain the same foothold that enabled the intrusion in the first place. Second, teams restore apps without rebuilding the identity and access layer that attackers used to move laterally and persist.
This is where “clean recovery” earns its keep. Clean recovery means you can answer three questions before you return to production:
- Is the data clean?
- Is the environment clean?
- Is the access path clean?
Sophos reports that 97% of organizations with encrypted data recovered it, yet backups were used in just 54% of incidents, and many still paid. That pattern fits what teams report after a real incident: data restore is possible, but confidence is missing. Confidence takes process, isolation, and validation.
What a Clean Recovery Workflow Looks Like
A clean recovery plan doesn’t need to be complex. But it does need to be disciplined. A workable approach looks like this:
- Freeze and scope the event: Preserve logs, ticket timelines, and core evidence. Keep this separate from the rebuild workstream so the rebuild doesn’t trample the forensic trail.
- Stand up an isolated recovery environment: Bring systems up in a locked-down space that does not have open connectivity back into production. Treat it like a quarantine zone.
- Restore “minimum viable business” first: Pick the smallest set of systems that lets the business operate: identity, core apps, core data services, and the few integrations that keep revenue and operations moving.
- Validate before promotion: Scan restored images, validate configurations, and confirm integrity checks. Rebuild credentials and keys. Re-issue admin access with clean devices and new secrets.
- Promote in controlled waves: Move validated systems into production in stages. Monitor authentication, endpoint behavior, and outbound traffic as systems return.
Stage2Data’s Clean Room recovery aligns with this operational need: a separate environment used to validate data and remediate threats before restoring business systems. It offers and isolated, air-gapped environment built with Cohesity, designed for validation and recovery without reinfection.
Network Reachability: DR Fails When the Network Doesn’t Fail Over
A recovery test that boots VMs proves one thing: your storage and compute can be provisioned elsewhere. It does not prove that customers, partners, and staff can reach those systems, or that systems can reach each other.
2025 fails frequently involved “Systems Up, Business Down” scenarios. While the VMs were running in a secondary site, the public-facing IPs, DNS records, and SaaS allowlists remained pointed at the dead primary site.
Network Recovery-as-a-Service (NRaaS) is the corrective measure for 2026. It ensures that when your compute fails over, your network reachability fails over with it, maintaining connectivity for users and partners without manual, emergency reconfigurations.
Treat Cloud as a Dependency, Not a Destination
Many organizations now depend on a single cloud tenant for primary workloads, immutable backups, identity services, and monitoring. That setup works until it doesn’t. 2025 saw a rise in tenant-level compromises where an attacker’s goal was cloud control plane access.
Cloud independence, or multi-cloud resiliency, is the only way to mitigate this. It means you can recover operations without being trapped inside one provider’s identity plane.
Join the Stage2Data Partner Program
The DRaaS market is growing fast, and MSPs have an incredible opportunity to lead the way. Partnering with Stage2Data means offering your clients more than just disaster recovery. It means giving them better value, service, and peace of mind—all while growing your own business.
Getting started is easy. Our team will guide you through the process, from initial setup to training and beyond. You’ll have access to the tools and support you need to succeed, all without the red tape that comes with larger providers.
What cloud independence looks like in recovery terms
A practical definition:
- You can restore workloads and data into an environment that the attacker didn’t control.
- You can run core business systems there long enough to stabilize.
- You can reconnect users and integrations without rebuilding everything from scratch.
Stage2Data’s Cloud Provider Resiliency (CPR) is a good example of replication and recovery from one cloud to another or to Stage2Data’s private cloud when a primary cloud environment becomes unavailable.
The value isn’t theoretical. Independence gives you options during the worst week of the year, when your normal platform becomes your constraint.
What to Ask Before You Trust a Recovery Plan
Use these 12 questions to pressure-test your own design, or to evaluate a partner.
- Where do we validate restored data and systems before returning to production?
- What stops reinfection during restore?
- Which identity systems must come up first, and how do we rebuild admin access safely?
- What happens to public IPs during failover?
- How do customers and partners reach us during failover without emergency reconfiguration?
- Do our LTR policies extend beyond the average attacker dwell time?
- Are our backups protected by Locked Object Storage that is inaccessible to primary domain admins?
- Which SaaS tools break if our outbound IP changes, and who owns those fixes?
- Where are backups stored, and who controls the keys and credentials?
- Can we recover into a different cloud or private environment and run there for days?
- How do we prove recovery, not just claim it?
- When did we last run a drill that included network, identity, apps, and third parties?
You’ll find that Stage2Data’s current offering responds clearly to these questions: Clean Room for validation and recovery confidence, network recovery-as-a-serivce (NRaaS) for network continuity during failover, and CPR for recovery options beyond a single cloud.
Final Thoughts
The 2025 reality check isn’t that ransomware is “getting worse.” It’s that basic recovery assumptions keep failing under pressure. Ransomware recovery is no longer defined by the speed of your backups; it is defined by the integrity of your strategy. While 2025 saw many organizations trapped in 100-day recovery cycles, 2026 presents an opportunity to shift toward verified victories. By moving away from single-tenant dependencies and adopting Locked Object Storage and LTR, we move beyond the hope of recovery and into the certainty of operations.
Victory in 2026 is defined by the ability to pivot. When a primary cloud tenant is compromised, we utilize CPR to maintain continuity. When a network goes dark, we rely on NRaaS to keep services reachable. When data integrity is questioned, we use the Clean Room to validate every file before it touches your production environment. This shift from reactive restoration to strategic resilience separates the organizations that survive an attack from those that lead through one.





